Hi all.
Recently I have come across numerous posts on LinkedIn touting the usefulness of Network Detection and Response (NDR) on its own as some kind of god-like security tool. The main issue I have with these types of tools is the fact people seem not realize that they are useless without real(and recent) context. For anyone in this space, you may have encountered rulesets such as ETPro and others, whereby they have various rule detections that trigger on traffic (such as C&C) based purely around the remote IP being flagged as "Malicious".
The fact is, in today's modern internet where IP addresses can be repurposed within hours and cloud infrastructure is ever-growing, purely basing your tool's detection and response on the equivalent of a file hash(but worse as hashes at least have continuity to some degree) without further research is a driver of "fake value" in the cybersecurity space. Typically these tools draw from numerous third-party reputation sites, but these are unreliable at best due to the fact so many IP addresses are part of external hosting infrastructure and are changed on the regular.
I like to think as NDR as a bit of a tree, going from somewhat reliable indicators to unreliable, let me showcase my drawing skills to exhibit this;
From the image, what I am trying to convey is that Raw IP addresses are possibly the worst identifier of malicious behavior from a pure connection-based standpoint. Let's take this site for example. If we plug our site into a common OSINT IP search like https://www.abuseipdb.com/ - for a start we receive numerous "community hits" for Nmap activity and other anomalous behavior -



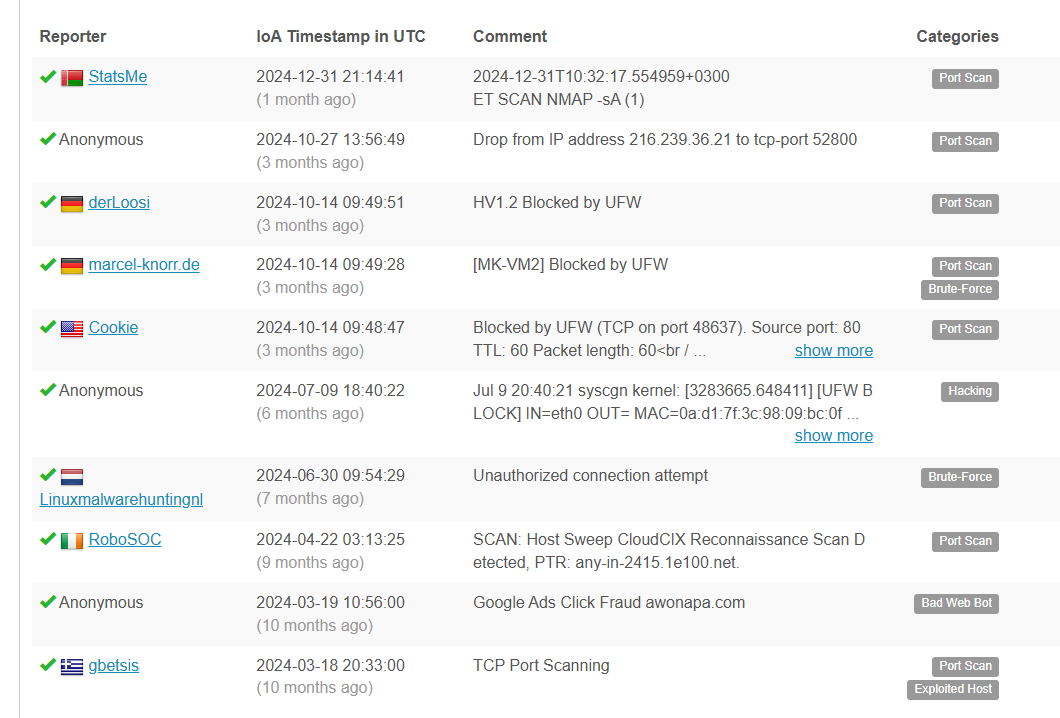

Comments
Post a Comment